Cybersecurity Framework – a walkthrough
As seen in the last blog, the Executive Order of the President of the United States calls for the development of a voluntary risk-based Cybersecurity Framework (CSF) – a set of industry standards and best practices to help organizations manage cybersecurity risks.
Building from those standards, guidelines, and practices, the CSF provides a common taxonomy and mechanism for organizations to:
- Describe their current cybersecurity posture;
- Describe their target state for cybersecurity;
- Identify and prioritize opportunities for improvement within the context of a continuous and repeatable process;
- Assess progress toward the target state;
- Communicate among internal and external stakeholders about cybersecurity risk.
The key leverage here is leveraging business drivers. This will ensure that the overheads are lesser and existing processes can be mapped to the CSF in three parts: CSF Core, CSF Profile, and CSF Implementation Tiers.
The CSF core essentially addresses a detailed layout of cybersecurity activities, outcomes, references, but at a policy level. It aligns industry standards and best practices to the CSF Core in a particular implementation scenario and supports prioritization and measurement while factoring in business needs. In a sense, the detail of CSF core guides while framing various CSF profiles. CSF Profiles help align business with resources, activities and ‘tolerance levels’. Finally, CSF tiers allow the organization to categorize the risk through understanding the characteristics of the approach of each CSF profile.
CSF core:
The CSF core divides the whole exercise into five major functions.
- Identify: What assets need protection?
- Protect: What safeguards are available?
- Detect: What techniques can identify incidents?
- Respond: What techniques can contain impacts of incidents?
- Recover: What techniques can restore capabilities?
CSF core helps alignment of functions, categories, and subcategories with business requirements, risk tolerance, and resources of the organization.
Feedback indicated the need for the CSF to allow for flexibility in implementation and bring in concepts of maturity models.
- Responding to feedback, CSF implementation tiers were proposed to reflect how an organization implements the CSF core functions and manages its risk.
- The tiers are progressive, ranging from partial (tier 1) to adaptive (tier 4), with each tier building on the previous tier.
- The tier characteristics are defined at the organizational level and are applied to the CSF core to determine how a category is implemented.
CSF enables organizations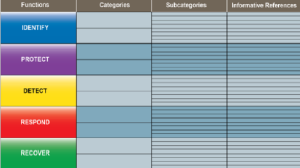 – regardless of size, degree of cybersecurity risk, or cybersecurity sophistication – to apply the principles and best practices of risk management to improving the security and resilience of critical infrastructure. CSF has to be customized to each organization as the nature of business, ecosystem, competition and threats are unique. The key point is to leverage existing processes and risk management practices and keep the overheads low. The essence of CSF is that it is a working document and has to be evolved through learnings. The Intel case study that we have enclosed is a great example of how learnings can be adopted while keeping the broad guidelines of CSF in mind.
– regardless of size, degree of cybersecurity risk, or cybersecurity sophistication – to apply the principles and best practices of risk management to improving the security and resilience of critical infrastructure. CSF has to be customized to each organization as the nature of business, ecosystem, competition and threats are unique. The key point is to leverage existing processes and risk management practices and keep the overheads low. The essence of CSF is that it is a working document and has to be evolved through learnings. The Intel case study that we have enclosed is a great example of how learnings can be adopted while keeping the broad guidelines of CSF in mind.
Risk Management and CSF:
Risk management is a key factor for any business. It is a continuous function of identifying, assessing, and responding to risk. To manage risk, organizations should understand the likelihood that a threat can happen and the impact it can cause. However, and the resulting impact. With this information, organizations can determine the acceptable level of risk for delivery of services and can express this as their risk tolerance.
With an understanding of risk tolerance, organizations can prioritize cybersecurity, enabling organizations to make informed decisions about cybersecurity expenditures. CSF uses risk management processes to enable organizations to inform and prioritize decisions regarding cybersecurity. It supports recurring risk assessments and validation of business drivers to help organizations select target states for cybersecurity activities that reflect desired outcomes. Thus, the CSF gives organizations the ability to dynamically select and direct improvement in cybersecurity risk management for the IT ecosystem.
We will examine of a case study of how Intel implemented this case study in our next blog.






Comments are closed.